Stop SQLi and XSS Attacks Easily with Traefik's WAF Integration

In today’s digital landscape, web applications and APIs are integral to virtually every aspect of modern life. From the familiar world of online shopping and social media to the behind-the-scenes functionality of mobile apps, government websites, and even entertainment platforms, APIs serve as the backbone of online interactions.
However, this ubiquity also makes them prime targets for cyber threats, and securing web applications and the flow of data that keeps our world running is a critical concern for enterprises. Malicious actors constantly search for vulnerabilities to exploit, aiming to steal sensitive data, disrupt operations, or even inject malware into unsuspecting systems. The exponentially increasing threat landscape demands a robust defense strategy, and that's where Web Application Firewalls (WAFs) come into play.
The Role of WAFs in API Security
WAFs are the first line of defense for your web-based applications and their APIs. They stand guard, meticulously examining every incoming request, ensuring only authorized and legitimate data passes through. WAFs prevent attackers from submitting malicious or unwanted data to applications as well as from exfiltrating sensitive data. Here's how they safeguard your business from a variety of threats:
- Known attack detection: WAFs recognize the signatures of common attack strategies employed by cybercriminals. These include attempts to exploit vulnerabilities like SQL injection (SQLi), Cross-Site Scripting (XSS), file inclusions, code injection, session hijacking, and even metadata or error leaks. By identifying these known threats, WAFs can effectively block them before they can cause you any damage.
- Beyond the obvious: Malicious activity isn't always so straightforward. WAFs can also detect abnormal or malformed requests deviating from regular user behavior. These red flags could indicate a more sophisticated attack, allowing the WAF to take preventative measures.
This level of protection provided by WAFs is crucial. But it doesn't stop there. WAFs offer additional functionalities to enhance security further:
- Virtual patching: Sometimes, vulnerabilities in your system might be identified before a permanent fix is available. WAFs can provide temporary protection by blocking exploits targeting those vulnerabilities, effectively plugging the hole until a proper patch can be deployed.
- Blocking malicious bots: The internet is rampant with automated bots. While some bots serve legitimate purposes, others can be malicious, launching denial-of-service attacks or scraping valuable data. WAFs can help filter out these malicious bots, keeping your APIs safe from unwanted traffic.
- Audit logging: Staying informed about potential security breaches is critical. WAFs provide valuable audit logs detailing matched rules and anomaly scores, allowing your security team to analyze potential threats and take appropriate action.
Beyond Technology: WAF as a Legal Necessity
In addition to protecting against cyber threats, WAFs are critical in helping enterprises meet various security standards and regulatory requirements. Many industries are governed by strict regulations that mandate specific security controls to protect sensitive data. Some of the most common standards that require or strongly recommend the use of WAFs include:
- Payment Card Industry Data Security Standard v4: Under PCI DSS 4.0, organizations must deploy an automated technical solution for public-facing web applications that continually detects and prevents web-based attacks. This is articulated in Requirement 6.4.2, which explicitly states that WAFs are no longer just a recommended practice but a must for compliance.
- Federal Risk and Authorization Management Program: FedRAMP requires stringent security controls for cloud service providers working with US federal agencies, including protections that WAFs can enhance.
- Health Insurance Portability and Accountability Act: While HIPAA does not explicitly require WAFs in the healthcare sector, it mandates the protection of electronic protected health information (ePHI), which can be supported by using WAFs to prevent unauthorized access and attacks.
- General Data Protection Regulation: Although GDPR requires appropriate technical and organizational measures to protect personal data, it does not explicitly mention WAFs. However, organizations should use them as part of their overall security posture to reduce the risk of data breaches that could lead to significant fines under GDPR.
To learn more about WAFs’ importance, check our detailed article: Why does WAF matter in API security?
However, keep reading if you’re curious about how Traefik can help you effortlessly mitigate these threats while complying with security standards.
A Free and Open-Source WAF in Traefik Proxy
The release of Traefik Proxy v3 marked a significant leap forward in enhancing application security through the introduction of two groundbreaking features: WASM-based plugins and the Coraza Web Application Firewall (WAF).
WASM (WebAssembly), a binary instruction format designed for efficient execution in web browsers, has found its way into the world of proxy servers. Traefik v3 embraces this technology, enabling developers to compile code in virtually any language into a portable format that runs seamlessly within the proxy environment. This innovation opened the door for a new breed of plugins, offering greater flexibility.
Capitalizing on this breakthrough, Traefik v3 introduced its first WASM-based plugin, the Coraza Web Application Firewall. Coraza is an open-source, Go-based WAF that has quickly become a favored choice for security-conscious enterprises. It stands out for its performance and endorsement by OWASP, a globally recognized authority on web application security.
Coraza is built on best practices and standards that are widely recognized in the cybersecurity community:
- It understands and can enforce rules written in ModSecurity’s Security Language (seclang). This compatibility is a significant advantage for organizations that are already familiar with ModSecurity, as they can easily transition to using Coraza without needing to rewrite existing security rules.
- Coraza comes equipped to enforce the OWASP Core Rule Set (CRS), a set of generic attack detection rules that protect against a wide range of threats. The CRS helps automate threat mitigation by blocking common attack vectors such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities, saving valuable time and resources.
The WASM-based Coraza WAF in Traefik is best suited for:
- One of the most compelling reasons to adopt a plugin-based WAF is to simply meet compliance requirements. A plugin-based solution like Traefik Proxy simplifies the process of implementing and managing security controls.
- Furthermore, a plugin-based WAF allows for granular protection. You can selectively apply WAF rules to specific pages or applications, such as protecting sensitive administrative areas like /admin while leaving less critical pages unfiltered. This approach optimizes performance and reduces the risk of false positives.
- A plugin-based WAF is particularly beneficial for organizations with internal applications that experience low traffic volumes but may still contain sensitive information. With Traefik Proxy, you can easily deploy and manage WAF protection for these applications without compromising performance or budget.
- Finally, filling in the cybersecurity skills gap is a significant challenge for many organizations. Attracting and retaining skilled security personnel is expensive and time-consuming. A plugin-based WAF like Coraza in Traefik Proxy can help address this issue by providing user-friendly configuration and baked-in rule sets based on best practices.
A 2023 study from the Information Systems Security Association (ISSA) indicates that 71% of companies report being severely affected by the shortage of skilled cybersecurity professionals. A plugin-based WAF can help bridge this gap by simplifying the management of API security.
Let’s illustrate how simple configuring the Coraza WAF WASM plugin is! Add this to your Traefik’s static configuration to load the plugin:
experimental:
plugins:
coraza:
moduleName: github.com/jcchavezs/coraza-http-wasm-traefik
version: v0.2.2
Then, leverage the WAF plugin in a middleware configuration. Using the Kubernetes CRD provider as an example:
---
apiVersion: traefik.io/v1alpha1
kind: Middleware
metadata:
name: coraza-waf-block-admin-path
namespace: apps
spec:
plugin:
coraza:
directives:
- SecRuleEngine On
- SecDebugLog /dev/stdout
- SecDebugLogLevel 9
- SecRule REQUEST_URI "@streq /admin" "id:101,phase:1,log,deny,status:403"
Then accessing /admin will return a 403 error as specified by the configuration rule, but everything else will return 200 as there is no matching rule. You’ll see its power even more when combining it with IP address checking, header-based filtering, or chaining any other middleware or plugin available for Traefik Proxy.
The plugin-based WAF offers a versatile solution for a variety of use cases. Its ease of use but still powerful capabilities make it an essential tool for organizations looking to secure their web applications in a cost-effective and manageable way. But if needs evolve and you need to juice out as much filtering from your WAF as possible, you’ll need a bigger wall.
A Performance-Optimized WAF for High-Volume APIs in Traefik Hub
Security needs become more complex as companies evolve and scale their digital infrastructure. While traditional solutions like application proxies serve many essential functions, they often fall short regarding advanced security requirements like advanced authentication and authorization. This is particularly true for organizations that rely on WAFs to protect their web applications and APIs. For them, transitioning from a simple application proxy to a more robust API Gateway, like Traefik Hub, can offer significant advantages, including enhanced security and vastly improved performance.
Traefik Hub represents the next step in the evolution of serving APIs, offering a comprehensive platform that goes beyond the capabilities of an application proxy. As a modern API Gateway and API Management solution, Traefik Hub is designed to handle the complex needs of today’s enterprises, providing advanced features such as its native WAF integration, which directly addresses the performance limitations many organizations face when using WAF plugins in a proxy setup.
The Need for a High-Performance WAF
One of the key challenges with using a WASM-based WAF plugin in Traefik Proxy is the performance overhead associated with the plugin. While WASM offers a flexible and portable way to deploy WAFs, it introduces certain inefficiencies that can impact the overall performance of the application:
- Boot-time overhead: Since WASM offers a secure runtime environment for plugins, the WASM binary associated with the WAF needs to be loaded at boot time for all middleware configurations. This loading process can delay application startup, especially in environments with complex configurations or high traffic demands.
- Run-time overhead: Once loaded, the WASM-based WAF analyzes each incoming request and outgoing response in real time. This continuous analysis introduces latency, which can slow down the request processing and reduce the application's overall efficiency. The performance overhead can become a significant bottleneck with high traffic volumes, limiting scalability and increasing operational costs.
To address these performance challenges, Traefik Hub offers a native WAF integration that eliminates the inefficiencies associated with WASM-based plugins. The native integration in Traefik Hub results in a WAF that is 23 times faster than its WASM-based counterpart in Traefik Proxy, providing a significant performance boost for your applications. You’ve read it correctly, not 23%, but 23 times!
The key to this performance improvement lies in the architecture of the native WAF integration in Traefik Hub. Unlike WASM-based plugins, the Coraza WAF codebase is natively integrated into Traefik Hub at compile time. Since no WASM runtime is involved in running the WAF, it eliminates the boot-time and run-time overhead associated with the plugin-based solution, resulting in faster startup times and more efficient request processing.
Benefits of a Native WAF Integration
The native integration of the Coraza WAF in Traefik Hub offers several significant benefits:
- Further enhanced security: The native WAF integration provides all the robust security features expected from Coraza, including protection against OWASP Top 10 vulnerabilities—but now with additional benefits. There’s no need to download the plugin during boot time, reducing the dependency on external components. This is perfect for air-gapped environments where external network access is restricted and enhances overall security by reducing the attack/risk surface.
- Simplified management and configuration: With native integration, managing security configurations becomes more straightforward, as there’s no need for static plugin configuration. Instead, security rules and configurations are handled only within the dynamic configuration.
- Improved performance and scalability: The native WAF integration allows for faster request processing, leading to better scalability. The same number of API Gateway replicas can handle more requests, improving resource utilization. This means you can run leaner infrastructure, serving the same or larger traffic with fewer resources, leading to lower operational costs.
Now, let’s see some proof of the claimed 23x performance improvement!
Performance Benchmark: WASM-Based vs. Native WAF
We conducted a performance benchmark to compare the efficiency of the native WAF integration in Traefik Hub against the WASM-based WAF plugin used in Traefik Proxy.
The benchmark results highlight the performance advantages of the native WAF in Traefik Hub:
- WASM-Based WAF: In our test environment, the WASM-based WAF managed to handle 29.04 requests per second.
- Native WAF: Under the same conditions, the native WAF processed a remarkable 683.34 requests per second.
This represents a 23.53x performance improvement when using the Coraza WAF natively in Traefik Hub!
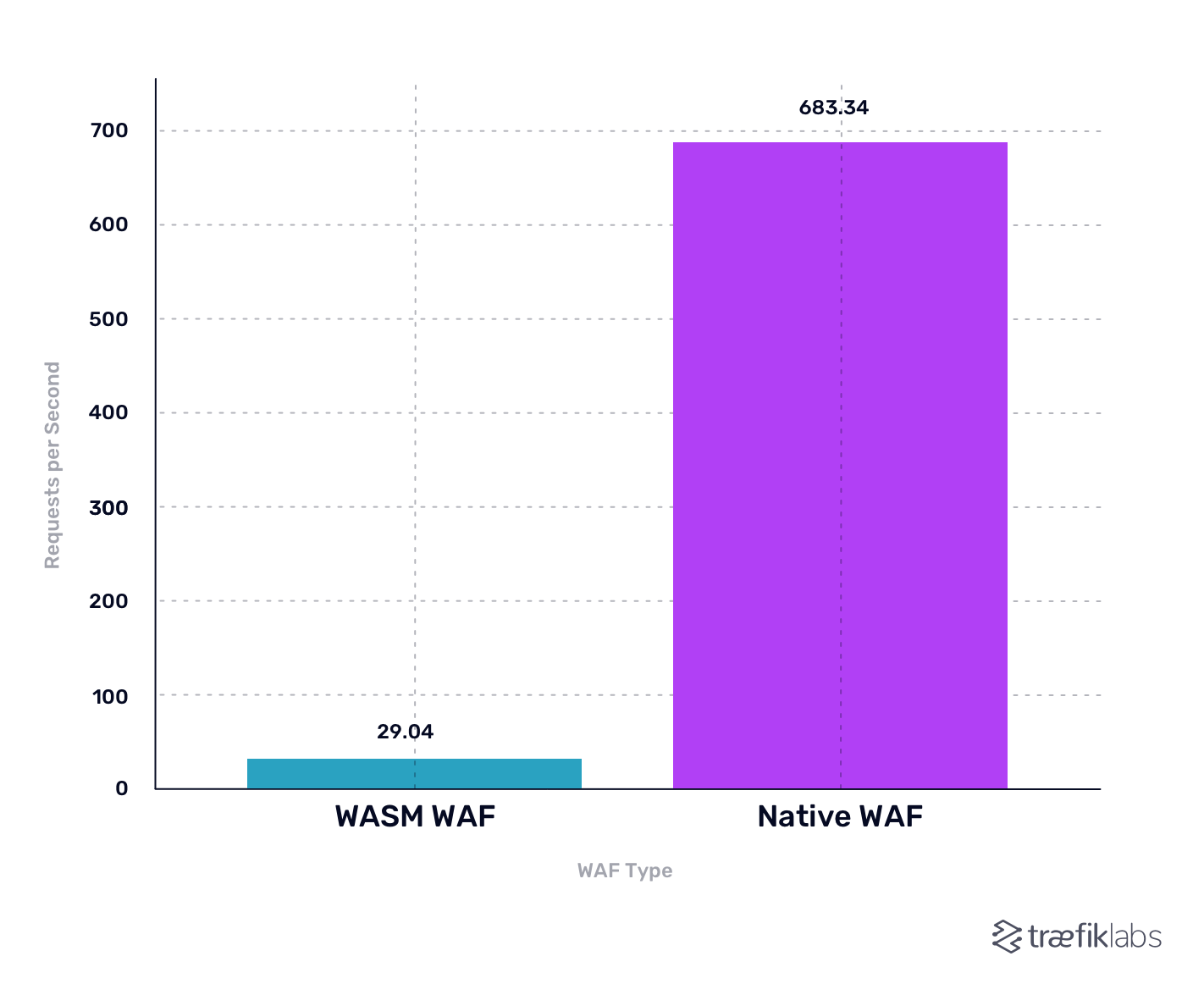
These metrics were obtained in a controlled environment using a local k3s cluster with just one gateway replica. While this setup provides a clear comparison of the two WAF approaches under identical conditions, it’s important to recognize that this is just one snapshot of performance as it is based on a simplified scenario and doesn't fully capture the capabilities of either the WAF or the API Gateway in a complex environment. The actual observed performance could vary depending on several factors:
- Scaling: In production, the API Gateway and WAF would probably be deployed with multiple replicas to handle higher traffic volumes in production. The native WAF's performance benefits would likely become even more pronounced in such scaled environments.
- Environment complexity: The nature of the applications, the complexity of the enforced security rules, and the overall architecture will all influence the WAF's performance.
- Resource allocation: Differences in CPU, memory, and other resource allocations between environments can also impact the measured throughput.
While the native WAF integration offers superior performance, it’s also essential to consider the trade-offs involved in running a WAF, even a high-performance one. Adding a WAF to your traffic processing pipeline introduces some overhead due to the need to inspect and potentially filter every request and response.
Our tests showed that disabling the WAF altogether could result in at least 4 times higher request throughput in Traefik Hub. This is an important consideration for organizations that must balance security with performance. For some applications or routes with lower security requirements, disabling the WAF might be acceptable to achieve higher performance.
However, for critical applications or sensitive data, the performance overhead introduced by a WAF is typically a necessary trade-off to ensure robust security. The key is to use the flexibility offered by Traefik Hub to apply the WAF selectively, protecting the most vulnerable parts of your infrastructure while maximizing performance where possible.
Migration from WASM-Based WAF to Native WAF
If you’re currently using the WASM-based WAF in Traefik Proxy, migrating to the Native WAF in Traefik Hub is straightforward. Just like other transitions within the Traefik ecosystem, this migration is designed to be seamless, allowing you to enhance your security setup without disrupting your existing configurations or workflows.
Traefik Hub has been built with user experience in mind, ensuring that the migration is as painless as possible:
- Remove static configuration: One key difference in the migration process is removing the static configuration required by the WASM-based WAF (the first block in the code example shown previously). The Native WAF in Traefik Hub does not require any static configuration, making the setup simpler and less prone to errors.
- Retain existing middleware configuration: The rest of your WAF middleware configuration will remain the same, so you won’t need to make any changes to your existing setup!
The migration process is quick and efficient, allowing you to immediately take advantage of the highly improved performance after upgrading from Traefik Proxy to Traefik Hub.
For more information on the WAF configuration options, check out the official Traefik Hub documentation.
Wrapping It Up
If you’re looking for tools to enhance your web application security within the Traefik ecosystem, the availability of Coraza WAF as a WASM plugin represents a significant step forward. It’s free and open-source, and you can start experimenting with it today within Traefik Proxy with optional commercial support.
When you feel you want more, Traefik Hub is equipped to handle the most demanding security requirements, providing both protection and performance at scale with its native WAF integration. You can easily migrate from plugin-based to native WAF through a smooth transition with further simplified configuration, keeping all your security defenses in place while optimizing your resource utilization with an outstanding 23x performance improvement. Visit our WAF solution page to learn more.
Ready to see how Traefik Hub can elevate your security strategy? Request a demo today and experience the benefits of a modern, high-performance API Gateway and Management solution.
In This Article




