7 Critical API Protection Strategies to Fortify Your API Security

API security isn't just good practice – it's a necessity. As businesses increasingly rely on APIs to power everything from mobile applications to cloud services and IoT devices, these digital interfaces have become the new perimeter – and the new target for sophisticated attackers.
The question isn't if an attack will happen, but when. A recent analysis by Treblle (2024) reveals a startling reality: over half of API requests analyzed in 2023 used no encryption whatsoever, leaving sensitive data exposed to interception. Even more concerning, 52% had no authentication mechanisms in place – essentially leaving the digital front door wide open. Furthermore, 85% of APIs implemented no rate limiting, making them vulnerable to brute force attacks and service disruptions.
These vulnerabilities aren't just theoretical concerns. High-profile breaches like the one experienced by BeyondTrust in late 2023, where API key exposure led to significant organizational damage, demonstrate the real-world consequences of inadequate security. As APIs continue to proliferate – with organizations deploying hundreds or even thousands across their ecosystem – the attack surface expands dramatically.
Compounding the problem is the rise of "zombie" APIs – those APIs that remain accessible but unmaintained. Treblle's analysis found that a staggering 35% of endpoints fell into this category, creating significant blind spots in security postures. Without proper documentation, oversight, or regular updates, these forgotten interfaces represent prime targets for attackers seeking the path of least resistance.
Against this backdrop of escalating threats and costly consequences, organizations need a comprehensive, multilayered approach to API security. Let's explore seven critical protection strategies that can help secure your APIs against emerging threats.
#1: Encrypt Your API Traffic
TLS certificates are free – so use them!
While HTTPS might seem basic, the data shows a shocking reality: 55% of API requests analyzed didn't use any encryption (Treblle, 2024). This means sensitive data is being transmitted in plaintext, vulnerable to interception.
Even if the topic feels a little arbitrary to mention, we should prioritize first and foremost to encrypt the traffic leaving or reaching the gateway.
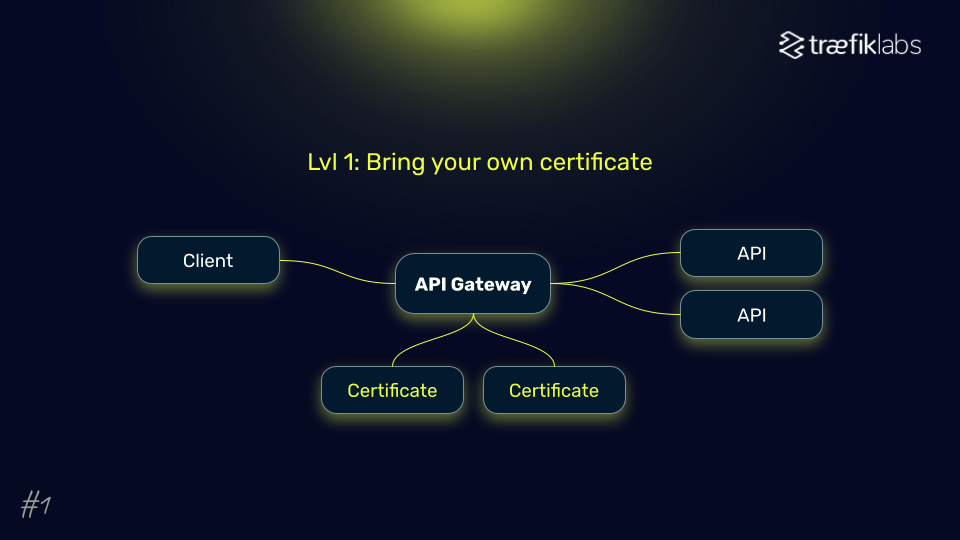
Protection levels:
- Manual certificate management: Suitable for organizations that purchase extended validity certificates from authorities
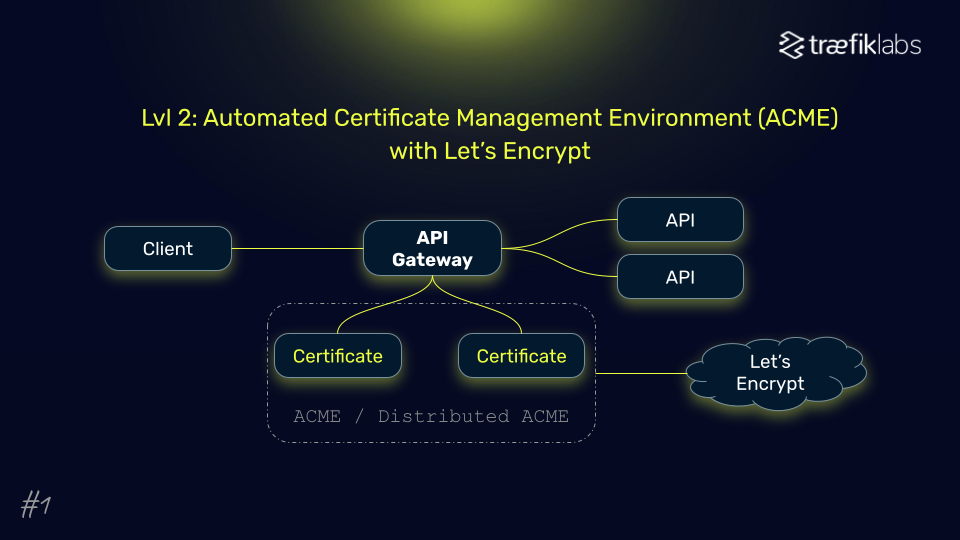
- Automated certificate management: Using solutions like Let's Encrypt with the ACME protocol
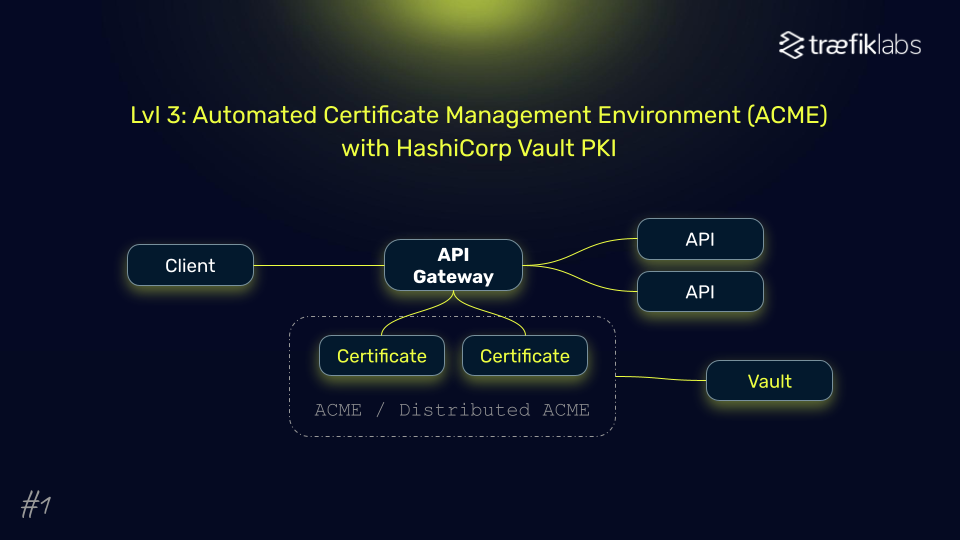
- Self-hosted private key infrastructure: Managing your own PKI with ACME-compatible tools like HashiCorp Vault
Remember, even internal APIs deserve dataflow encryption. There is no excuse for internal APIs to be left unsecured. Leverage wildcard certificates to protect subdomains that are only resolvable through an internal DNS server.
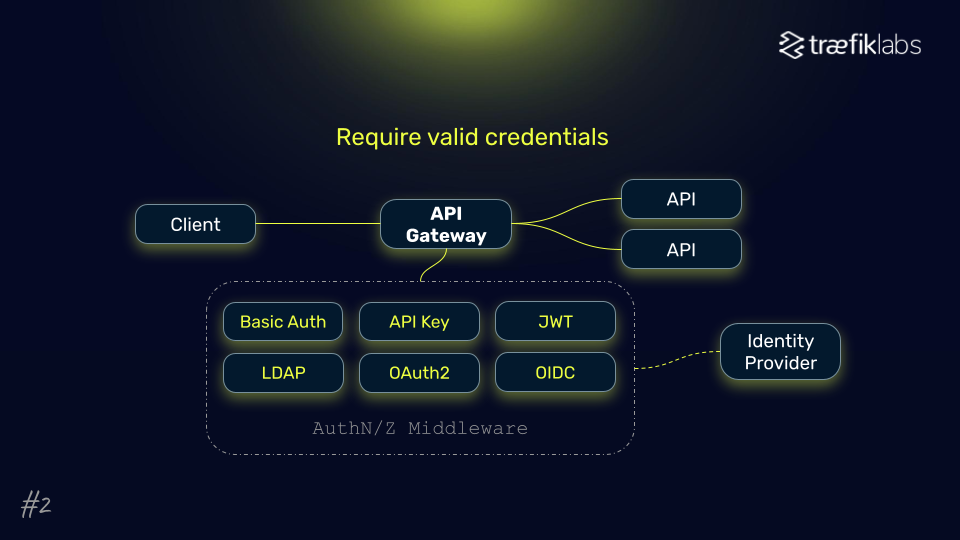
#2: Enforce Strong Authentication and Authorization
The data from Treblle revealed that 52% of analyzed requests had no form of authentication in 2024. This amount represents a massive vulnerability surface. Even internal infrastructure isn't immune to threats. Recent breaches like the one experienced by BeyondTrust demonstrate that API keys can be compromised with devastating effects.
Unauthenticated API calls should be the exception, a deliberate choice that you don't put any kind of authentication in front of them. Apart from these choices, you should authenticate everything.
The best approach starts with an identity provider as the foundation layer for proper API governance, with related authentication methods like JWT, OIDC, or OAuth2 building on top of it.
#3: Protect APIs From Abuse and Overuse
Avoid service disruptions, protect performance, user trust & SLAs
Despite the fundamental role of rate limiting in API security, a surprising 85% of analyzed APIs had no rate limits in place, leaving them vulnerable to denial-of-service attacks and excessive usage (Treblle, 2024). This widespread oversight exposes systems to severe disruptions, impacting both operational stability and user experience.
There are several layers of protection available to prevent such vulnerabilities. To name a few:
- IP Address Filtering: This method restricts access to specific IP ranges, ensuring that only trusted sources can make requests.
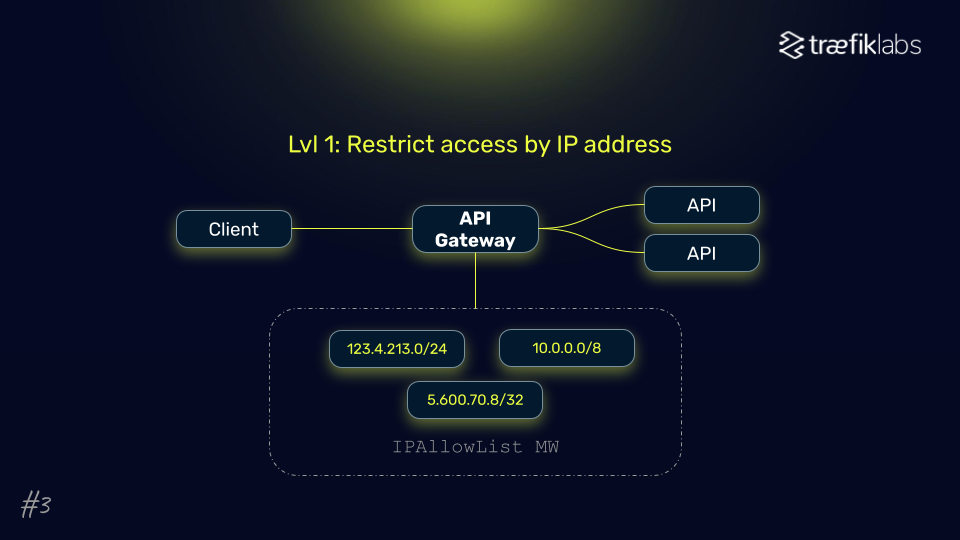
- Parallel Request Limitation: By controlling the number of concurrent requests from a single client, systems can prevent overloads and maintain optimal performance. Especially useful to fight web crawlers or DoS attacks.
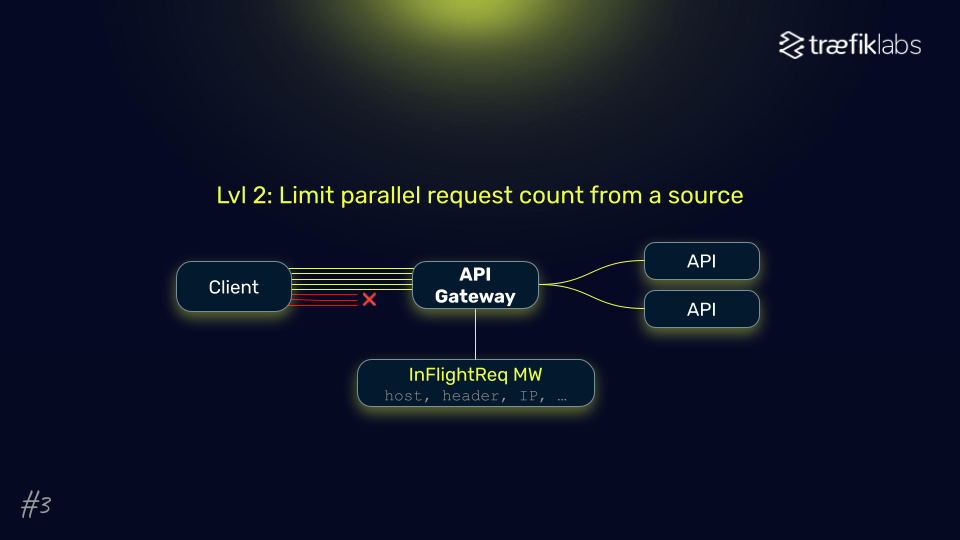
- Request Flow Control: Implementing true rate limiting with token bucket algorithms helps manage request rates effectively, thereby preventing abuse.
- Distributed Rate Limiting: This approach shares rate limit counters across gateway replicas, ensuring consistent enforcement of limits even in distributed architectures. Every replica sees the same counters, enhancing security through coordinated rate limiting.
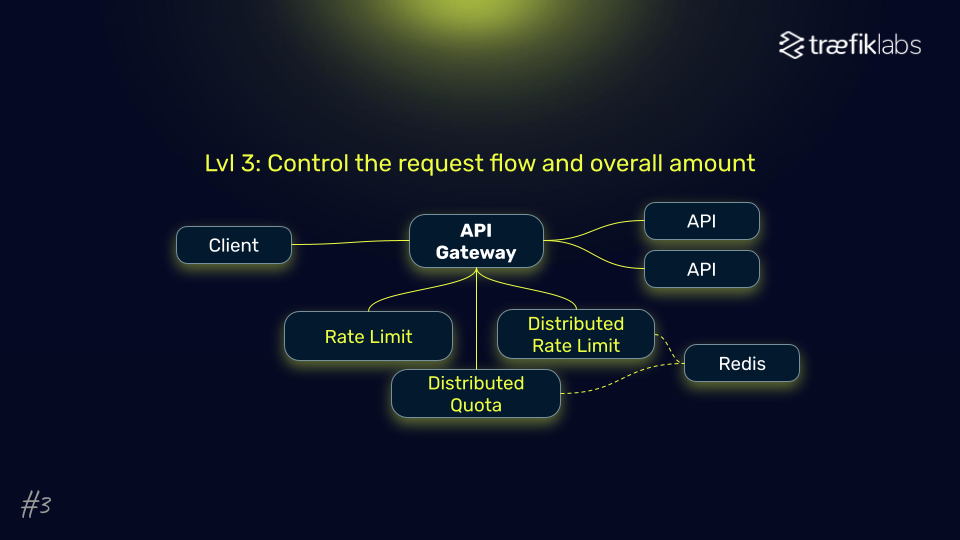
By leveraging these layered protections, organizations can significantly level up their security game, reducing the risk of service disruptions and safeguarding user trust.
#4: Block Known Vulnerabilities
Configure a Web Application Firewall (WAF)
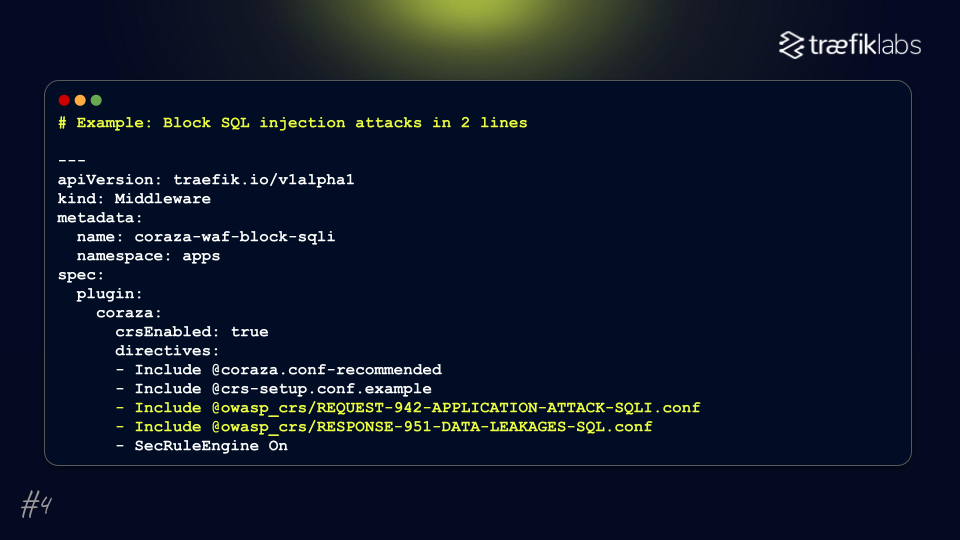
A Web Application Firewall (WAF) is crucial for defending against known attack patterns, including SQL injection and cross-site scripting. Beyond protecting sensitive data, a WAF is also essential for maintaining regulatory compliance, such as PCI DSS requirements.
Traefik Labs utilizes an open-source core for its firewall, which has OWASP endorsement, ensuring industry-standard protection against the latest threats. Deploying a WAF is relatively straightforward, often requiring just a few lines of configuration, making it an accessible yet powerful mechanism for enhancing security.
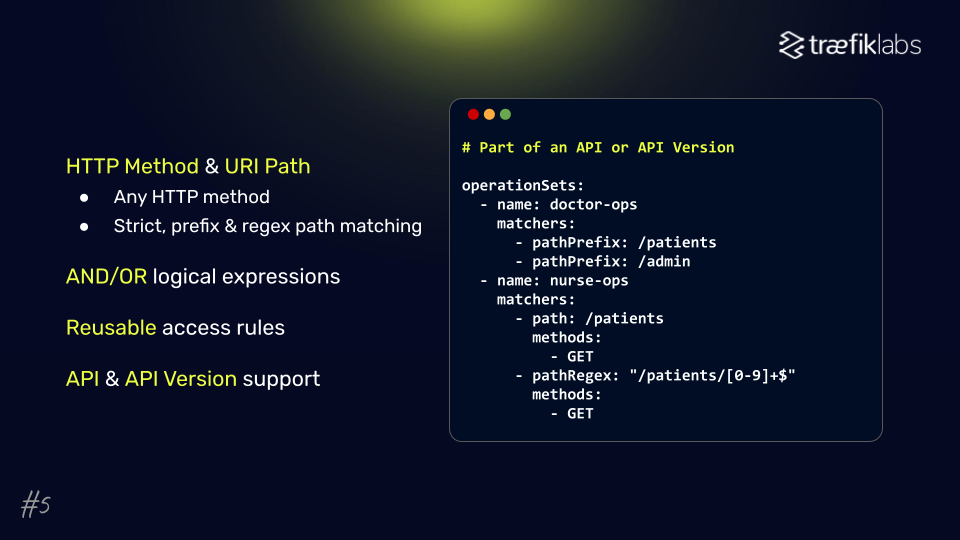
#5: Apply Zero-Trust for Accessing APIs
Avoid data leaks with the least privilege principle
Rather than providing unrestricted access to entire APs, a zero-trust approach restricts access to specific endpoints and methods, enhancing security by enforcing least-privilege access, significantly reducing APIs' attack surface.
By defining granular access rules, you can control exactly what clients can access, even as your APIs evolve. This ensures that newly deployed endpoints are not automatically exposed, minimizing the risk of unauthorized access.
#6: Centralize Secret and Key Management
Protect API Keys for AI/LLM APIs
With the growing reliance on external services, particularly AI and LLM services that require API keys for access, centralizing API key management has become crucial. These keys are powerful – if compromised, they can allow unauthorized users to exhaust tokens, deplete account credits, or even drain linked bank accounts.
The most effective solution is to store credentials centrally and issue short-lived tokens to end users. These tokens can be easily revoked, minimizing the impact of compromised keys. By implementing this gateway pattern, organizations can prevent the direct exposure of valuable API keys, ensuring better security and control.
Centralized API key management not only safeguards sensitive data but also streamlines the administration of access credentials.

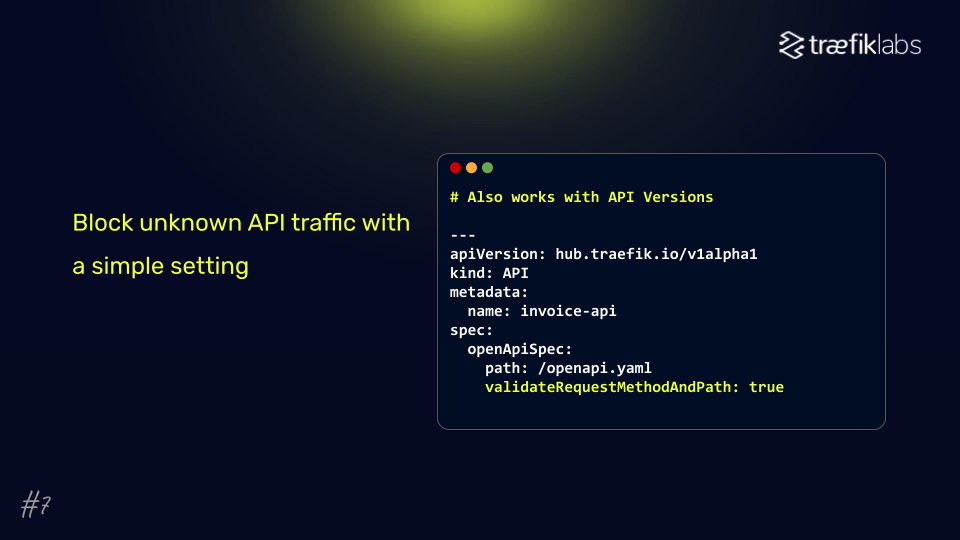
#7: Avoid Zombie and Shadow APIs
Only expose what’s documented in your OpenAPI specification
One of the most alarming findings showed that 35% of API endpoints were "zombie" endpoints – accessible but unmaintained and potentially vulnerable (Treblle, 2024).
These unmaintained APIs pose more and more threats to organizations these days. Use OpenAPI specifications to define legitimate endpoints and block everything else. Even for legacy systems without documentation, observability tools can help build specifications from observed traffic. You can block undocumented endpoints with flipping one single configuration value.
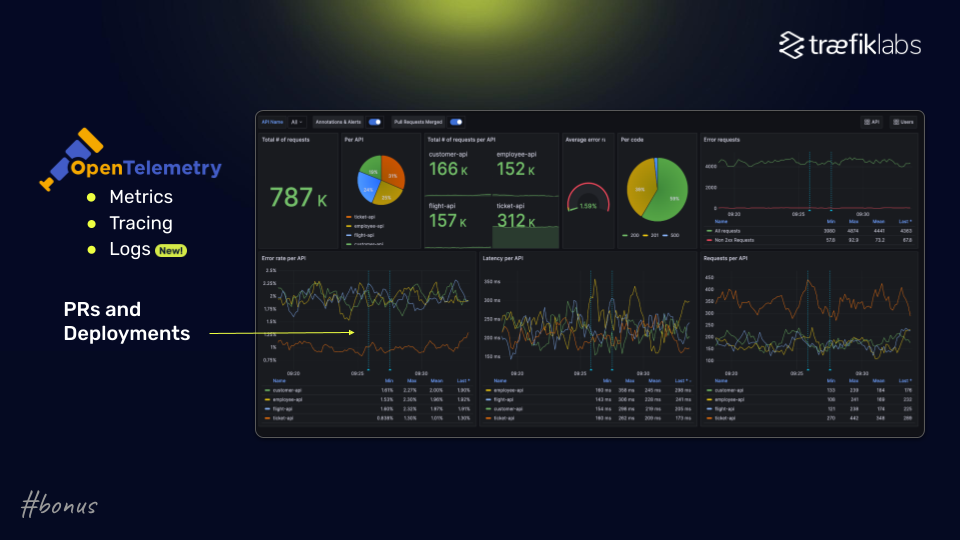
Bonus Tip: Implement Comprehensive Observability and Reduce Downtime Dramatically
While not directly a security control, observability provides the visibility necessary to identify potential threats and respond quickly.
Without this, you will not see if request rates spike up, if error rates spike up, or if an IP address bombards your infrastructure. By implementing OpenTelemetry for metrics, tracing, and logs, organizations can identify potential security incidents and correlate them with changes to systems. This visibility is essential for effective incident response.
Taking a Multilayered Approach
No single security measure is sufficient on its own. To effectively safeguard APIs, organizations should adopt a multilayered security strategy, integrating multiple protective mechanisms. Each layer – be it rate limiting, WAF, zero-trust, centralized key management, or observability – provides unique benefits that collectively enhance the security posture.
These measures are designed to work together, reinforcing each other to create a robust defense system. By implementing this comprehensive approach to API security, organizations can significantly reduce their risk profile, protecting their data and systems from emerging threats.
The multilayered strategy ensures a resilient and secure API environment, safeguarding business operations and maintaining user trust.
This article was contributed to DevOps.com by Traefik Labs for KubeCon London 2025.
Ready to see how Traefik Hub can elevate your security strategy? Request a demo today and experience the benefits of a modern, high-performance API Gateway and Management solution.
In This Article
- #1: Encrypt Your API Traffic
- #2: Enforce Strong Authentication and Authorization
- #3: Protect APIs From Abuse and Overuse
- #4: Block Known Vulnerabilities
- #5: Apply Zero-Trust for Accessing APIs
- #6: Centralize Secret and Key Management
- #7: Avoid Zombie and Shadow APIs
- Bonus Tip: Implement Comprehensive Observability and Reduce Downtime Dramatically
- Taking a Multilayered Approach




