The AI Triple Security Gap: Why Your Gateway Strategy is Already Obsolete
MCP Changes Everything, and Most Security Teams Don't Know It Yet
The enterprise AI landscape just experienced a seismic shift. Anthropic's Model Context Protocol (MCP) has rapidly become the de facto standard for how AI agents interact with enterprise tools, data sources, and APIs. Within months of its release, MCP achieved what typically takes years: widespread adoption across major agent frameworks and AI development platforms, with thousands of MCP servers now deployed across the ecosystem.
But here's the problem: MCP introduces attack surfaces that traditional API security was never designed to handle.
While security teams focused on securing their APIs, a new threat vector emerged. Malicious instructions hide in prompts, legitimate tools transform into data exfiltration mechanisms overnight, and AI agents can be manipulated into bypassing every security control you've carefully implemented.
The uncomfortable truth: If your security strategy relies solely on API gateways, you're protecting the wrong layer.
Your Critical Data is Now Agent-Accessible
The MCP ecosystem is expanding at an unprecedented pace across enterprise infrastructure. Within months of release, hundreds of MCP servers have been deployed, with new implementations appearing weekly. Here's what's already agent-accessible through verified MCP server implementations:
Databases & Data Stores: Oracle DB23ai (official SQLcl MCP server), PostgreSQL, MySQL, MongoDB, SQLite, Redis, InfluxDB, CockroachDB, and other popular database systems
Data Warehouses & Analytics Platforms: Snowflake (official Cortex AI integration from Snowflake-Labs), BigQuery, Databricks, Apache Druid, and modern data platforms
Cloud & Developer Platforms: Salesforce (official DX MCP Server and community implementations), AWS services (CloudTrail, Bedrock, CDK), Supabase, Heroku, Firebase, and Cloudflare Workers
Collaboration & Communication: Google Drive, Slack, GitHub, Linear, Notion, Intercom, and productivity platforms
File Systems & Storage: Local filesystems with configurable access controls, cloud storage services, and document repositories
Development & DevOps Tools: Git repositories, CI/CD pipelines, container platforms, observability systems, and infrastructure-as-code tools
This isn't some distant future. It's happening right now. The MCP ecosystem is growing exponentially, with community and official implementations appearing across every category of enterprise software. Your perimeter security remains essential, but it's no longer sufficient once autonomous agents can chain multiple tools together across different systems before any single control point can see the complete attack.
The Critical Gap
Take database MCP servers as an example: they typically run with their own static database connection credentials, exposing tools that let AI assistants execute queries. The pattern is consistent across implementations. Authorization operates at the database connection level, and whatever the MCP server's authenticated user can do determines what the agent can do.
That's true, and it perfectly crystallizes the gap. Once connected, authorization collapses to the authenticated principal. There's no agent-aware control over specific tools, methods, or parameters before execution, nor any governance over the non-database tools the agent might chain together in the same session.
This pattern repeats across every MCP server type. Database MCP servers inherit database user permissions. Salesforce MCP servers inherit the user's CRM role and permissions. Cloud platform MCP servers inherit the authenticated user's access scope. File system MCP servers inherit filesystem permissions. GitHub MCP servers use the personal access token's full permissions. Slack MCP servers can access any channel the token allows.
The Attack Scenario: Cross-System Data Exfiltration
Consider this realistic attack: "Summarize sensitive customer data and share it externally"
Without proper controls, the attack unfolds across multiple systems. First, the Slack MCP Server reads confidential customer discussions from private channels. Next, the Salesforce MCP Server queries opportunity data with revenue projections. Then the Google Drive MCP Server accesses strategic planning documents. Finally, an HTTP tool posts the consolidated summary to an external webhook. Your competitive intelligence is gone.
Why traditional security fails here: The attack chain spans multiple systems (Slack, Salesforce, Google Drive, and external HTTP) that your individual system security controls can't govern holistically. Each individual access looks legitimate. The combination is malicious.
The Triple Gate Pattern: Defense in Depth for AI
The cloud-native community learned this lesson with containers: layered defense beats perimeter security. We didn't secure Kubernetes with a single firewall. We built defense in depth with network policies, pod security standards, RBAC, and admission controllers.
AI agent security demands the same architectural rigor.
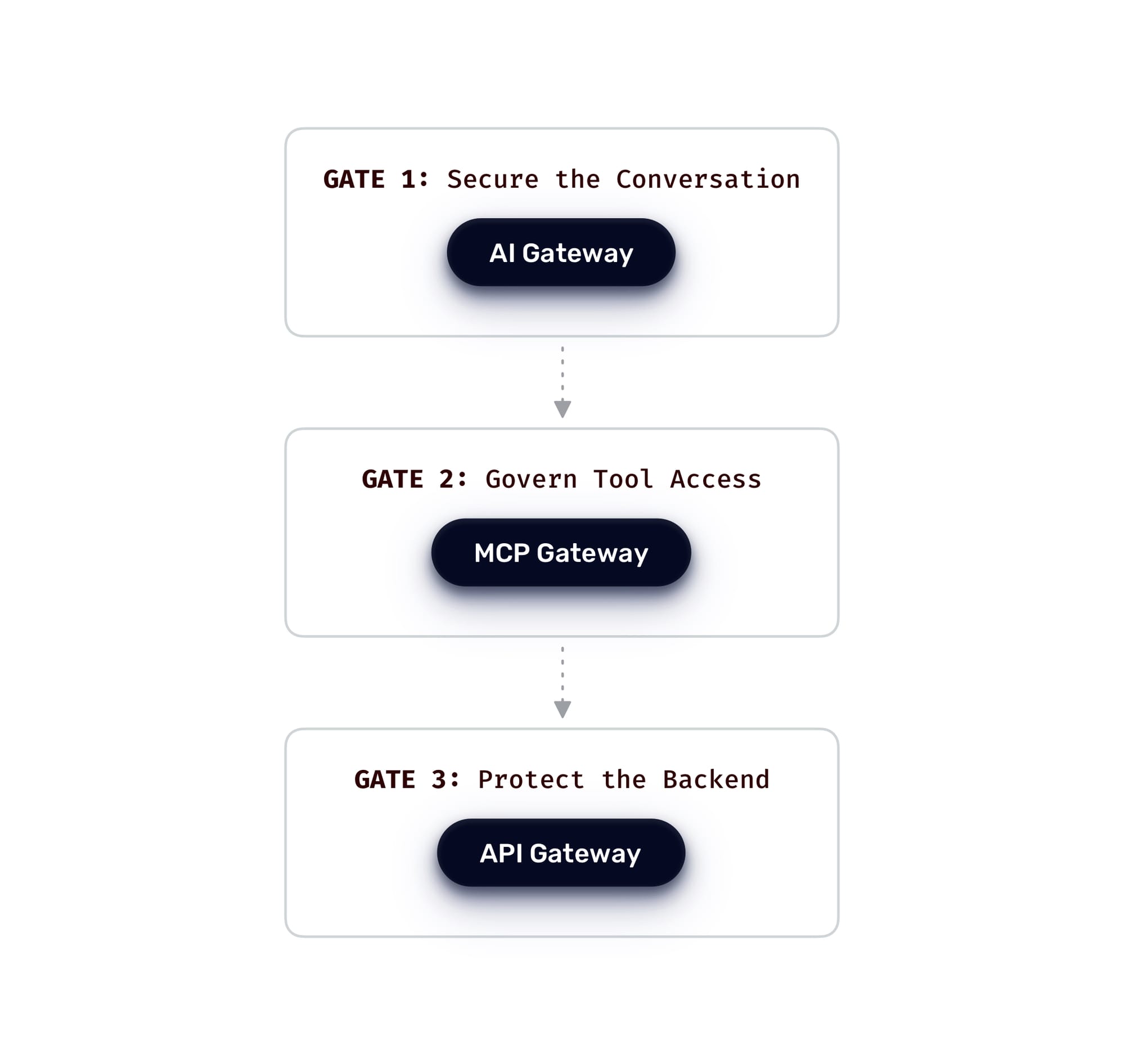
Each gate enforces policies appropriate to its layer. Unlike single-gateway approaches, attacks must defeat all three gates simultaneously to succeed, dramatically reducing your attack surface.
Gate 1: AI Gateway (Securing the Conversation)
The problem starts at the conversation layer. Attackers don't need to break your encryption or steal credentials anymore. They just need to convince your AI agent to do their bidding. Traditional security tools can't help here because they were built for APIs, not conversations with language models.
This is where Traefik fundamentally changes the game. Instead of relying on a single AI security model or vendor, Traefik orchestrates multiple specialized AI models into a unified policy enforcement pipeline. Think of it as having multiple security analysts, each trained to spot different attack patterns, all working in concert.
Topic control models detect when someone's trying to extract data or integrate with external systems. Content safety models identify privacy violations across more than 22 categories of sensitive information. And jailbreak detection models catch the sophisticated attempts to bypass your AI's restrictions, the digital equivalent of social engineering.
The key advantage? Unlike point solutions or cloud-based AI services that force you to send your data elsewhere, Traefik's entire security pipeline runs in your infrastructure. Deploy GPU-accelerated models like NVIDIA NIMs for maximum performance, integrate your custom classifiers trained on your specific threats, or combine multiple vendors' models. All without changing your architecture. No external API calls putting your data at risk. No vendor lock-in constraining your choices. Just one unified policy layer that adapts to your needs.
This gate blocks prompt injection attacks, jailbreak attempts, PII extraction requests, off-policy conversations, and inappropriate interactions before they ever reach your AI systems.
Gate 2: MCP Gateway (Governing Tool Access)
The MCP protocol presents a unique challenge. By design, it delegates all access control to implementers, creating what amounts to a protocol-level security vacuum. The specification is refreshingly honest about this, explicitly stating that "the core protocol lacks standardized permission or sandbox mechanisms."
This deliberate gap demands a new approach to authorization. Traditional access control models fail spectacularly when applied to AI agents.
Why Traditional Access Control Fails for AI Agents
Consider RBAC: agents don't have job titles or departments. When an agent inherits a "sales manager" role in Salesforce, it suddenly has access to all opportunities, all forecasts, and all customer data across the entire organization. That's absurd when all it needs to do is send follow-up emails to customers who haven't responded in 30 days.
ABAC seems better at first, since you can add context like time and location. But as you add more attributes, the complexity explodes exponentially. Try managing attribute combinations for hundreds of autonomous agents accessing dozens of different systems, each with their own attribute schemas. It quickly becomes an opaque mess that no one can audit or understand.
Delegation and impersonation make things even worse. When an agent impersonates a user across Salesforce, Google Drive, and Slack simultaneously, tracking who's responsible for what becomes nearly impossible. The audit trail
turns into fiction, and agents routinely gain access far beyond what any single task requires.
The fundamental issue is that these models were designed for human users with relatively stable, role-based permissions. They assume someone clocks in at 9 AM with a fixed set of responsibilities. AI agents need different access across different systems for different workflows, often changing by the minute.
How TBAC Works: Three Dimensions of Control
This is why we developed Task-Based Access Control (TBAC), a new authorization paradigm that focuses on the work being done rather than the identity doing it. TBAC creates a progressive permission funnel through three dimensions:
-
📋 Tasks (High-level business objectives): Tasks represent business-level goals and intent like
customer_followup, generate_sales_report, or resolve_support_ticket. This is the coarsest filter and your first gate. Before considering which systems the agent can access, you validate that the agent is authorized to perform this type of business work at all. An agent without thefinancial_reportingtask can't even begin to access financial systems, regardless of what specific tools it might need. -
🔧 Tools (System and resource access): Tools control which specific MCP servers and their exposed resources the agent can access. Even if an agent is authorized for the
customer_followuptask, it doesn't get blanket access to all systems. Instead, it receives precisely scoped access to specific MCP servers (salesforce_crm,email_service) and their individual tools/methods (query_opportunities,send_email). Your customer follow-up agent might need Salesforce's opportunity queries and email capabilities, but has no business accessing theexport_all_datatool or yourgoogle_driveserver with financial documents. -
💰 Transactions (Granular runtime controls): This finest-grained layer validates the specific parameters and context of each operation. It's not just "can this agent query Salesforce opportunities" but "can it query opportunities with these specific filters at this time from this location?" Transactions act as runtime guardrails, preventing dangerous operations even when the agent has legitimate access to the tool. They block queries without filters, updates to protected fields, or operations that could exfiltrate large datasets.
# An example JWT schema
{
"sub": "<target agent>",
"tasks": ["<list of tasks>"],
"tools": {
"<mcp server>": {
"actions": ["<action names>"],
"filters": { <additional transaction filters> }
}
}
}
These three dimensions work as a progressive permission funnel. First, validate the business objective (task). If authorized, validate which systems and specific tools can be accessed (tools). Finally, validate the specific operation parameters and context (transactions). Each layer further constrains what the agent can do, ensuring minimum necessary permissions across all enterprise systems.
The Innovation: Dynamic Variable Substitution
Here's where traditional policy systems break down completely. Want to give agent-123 access to Salesforce? You write a policy. Does it also need Google Drive? Another policy. Add agent-456 with different permissions? More policies. Scale this to hundreds of agents accessing dozens of systems, and you're drowning in thousands of policy rules that become impossible to maintain or audit.
Traefik flips this entire model through JWT claim and MCP parameter substitution: ${jwt.claim_name} and ${mcp.parameter_name}.
Now one policy works for every agent:
policies:
# Task-level authorization
- match: "Contains(`jwt.tasks`, `${mcp.params.task}`)"
action: allow
# Tool-level authorization
- match: "Contains(`jwt.allowed_tools`, `${mcp.params.name}`)"
action: allow
# Transaction-level constraints
- match: |
Equals(`mcp.params.name`, `query_opportunities`) &&
Contains(`jwt.tools.salesforce_crm.allowed_fields`, `${mcp.params.field}`)
action: allow
The same policy line works for every agent. Their specific permissions come from their JWT token issued by your existing identity provider or any OAuth compliant provider like Okta, Azure AD, Auth0, Keycloak, etc. No more policy explosion. No more maintenance nightmare.
Real-World Example: Customer Follow-Up Campaign
Let's see how this works in practice. A sales agent needs to query recent opportunities in Salesforce, draft follow-up emails based on templates in Google Drive, and log activities back to Salesforce. Nothing else.
The JWT token structure defines exactly what this agent can do:
{
"sub": "agent:sales-followup-bot",
"tasks": ["customer_followup"],
"tools": {
"salesforce_crm": {
"actions": ["query_opportunities", "create_activity"],
"filters": {"status": "Open", "days_since_contact": ">30"}
},
"google_drive": {
"actions": ["read_file"],
"allowed_folders": ["email_templates"]
},
"email_service": {
"actions": ["send"],
"allowed_domains": ["customer.com", "prospect.com"]
}
}
}
The JWT token acts like a security badge that precisely defines what the sales agent can do. The tasks field authorizes only customer follow-up work (not financial reporting or other business functions). The tools section grants access to specific systems and their methods: Salesforce access is limited to querying open opportunities inactive for 30+ days and logging activities. Google Drive access is restricted to reading only the email templates folder, not financial documents. Email capabilities are constrained to sending messages only to customer domains, not internal addresses. Each nested level further restricts permissions, creating an airtight scope for this specific workflow.
The result? The agent completes its workflow with precisely scoped permissions across all three systems. If compromised, it cannot access closed deals or sensitive forecast data in Salesforce. It cannot read financial planning documents in Google Drive. It cannot send emails to internal company addresses. And it cannot access Slack, databases, or any other MCP servers.
GitOps Governance Layer
Beyond runtime enforcement, every MCP server undergoes human validation before deployment. Tool definitions are stored in Git, requiring approval before reaching production. Change detection alerts trigger when tool behavior deviates from the approved baseline. And a complete audit trail tracks who approved what, when.
This blocks tool poisoning attacks (malicious instructions in descriptions), rug pull attacks (tools that transform after approval), tool shadowing (malicious tools with identical names), privilege escalation, cross-system data aggregation attacks, and configuration drift.
Gate 3: API Gateway (Protecting the Backend)
Even with Gates 1 and 2 in place, MCP servers eventually call your backend APIs, databases, cloud services, and enterprise systems. These underlying services need their own layer of protection.
Traefik's battle-tested API management capabilities provide this final defensive layer. Centralized credentials management automatically injects service credentials, rotates tokens, and manages authentication to backend APIs without exposing secrets to MCP servers. Fine-grained API authorization ensures agents can only invoke authorized endpoints. Distributed rate limiting protects backend services from overwhelming request volumes with intelligent throttling across your infrastructure.
API plans and subscriptions define consumption quotas and access tiers for different agent types, preventing resource exhaustion. Operation filtering exposes only specific API operations to agents, hiding sensitive or administrative endpoints. TLS/mTLS prevents man-in-the-middle attacks with encrypted transport and mutual authentication. Input validation sanitizes requests before they reach vulnerable servers. And DLP-style inspection detects sensitive data patterns in responses before they leave your infrastructure.
This comprehensive protection blocks network-level attacks, API abuse and resource exhaustion, unauthorized endpoint access, command injection attempts, SSRF attacks, credential theft and token leakage, and traditional API vulnerabilities.
How the Triple Gate Stops the Attack
Let's return to our cross-system exfiltration scenario and trace exactly how each gate responds to the threat: "Summarize sensitive customer data and share it externally."
The first line of defense activates at the AI Gateway. The topic control model immediately recognizes the dangerous pattern: data extraction combined with external sharing targeting sensitive information. Before the request even reaches your AI model, it's blocked with a 403 Forbidden response.
But sophisticated attackers don't give up that easily. They'll try to obfuscate their intent, perhaps breaking the request into seemingly innocent pieces. That's when the content safety model steps in, trained to identify privacy violations even when they're cleverly disguised. And if that fails? The jailbreak detection model catches the manipulation attempt, recognizing the linguistic patterns that indicate someone's trying to bypass restrictions.
Even if an attacker somehow slips past all three AI-level defenses (perhaps through a zero-day prompt injection technique), they hit the MCP Gateway's TBAC enforcement. Now they face a completely different challenge. The agent's token only authorizes customer_followup tasks, not data aggregation. Its tool allowlist explicitly excludes access to Google Drive's strategic documents. The Salesforce query filters prevent any access to sensitive forecast data. HTTP tool calls to external domains are blocked entirely. And cross-system data correlation? Impossible with the scoped permissions.
Should the impossible happen and the attack penetrates both previous layers, the API Gateway provides the final line of defense. Rate limiting algorithms detect the unusual data access patterns. Why is this agent suddenly reading hundreds of customer records? DLP inspection identifies sensitive data patterns in the aggregated responses, blocking them before they can leave your infrastructure. And egress controls ensure that even if everything else fails, that external webhook destination remains unreachable.
Five independent security layers, each operating on different principles, each capable of stopping the attack on its own. That's defense in depth.
Threat Coverage at a Glance
| Attack Vector | Without Triple Gate | With Triple Gate |
|---|---|---|
| Prompt Injection | ❌ Undetected | ✅ Blocked (AI Gateway) |
| Tool Poisoning | ❌ Executes | ✅ Blocked (AI Gateway + GitOps) |
| Cross-System Data Exfiltration | ❌ Succeeds | ✅ Blocked (All Three Gates) |
| Rug Pull Attacks | ❌ Transforms unnoticed | ✅ Detected (Change Alerts) |
| Tool Shadowing | ❌ Hijacks requests | ✅ Prevented (Namespacing) |
| Privilege Escalation | ❌ Full access | ✅ Blocked (TBAC) |
| External Data Sharing | ❌ Posts externally | ✅ Blocked (MCP Gateway) |
| API Abuse & Resource Exhaustion | ❌ Overwhelms backends | ✅ Blocked (Rate Limiting + Quotas) |
| Unauthorized Endpoint Access | ❌ Accesses admin APIs | ✅ Blocked (Operation Filtering) |
| Credential Theft | ❌ Exposes secrets | ✅ Prevented (Upstream Auth) |
| MITM Attacks | ❌ Intercepts traffic | ✅ Blocked (TLS/mTLS) |
Why One Unified Platform Matters
The Problem with Fragmented Tools
Deploying standalone AI security, MCP governance, and API gateway tools creates operational nightmares that compound over time.
Attack chains span multiple systems. When an attack moves from Salesforce to Google Drive to Slack to an external webhook, you're correlating logs from three different security products across different formats and timelines. By the time you piece together what happened, the damage is done.
Policy conflicts become inevitable. The AI gateway allows a request, the MCP gateway blocks it, but the API gateway allows it again. Who wins? How do you debug this? Which team owns the resolution?
Configuration drift accelerates with every product you add. Three products mean three configuration languages, three deployment pipelines, and three teams managing different policies. What starts as minor inconsistencies becomes major security gaps.
The blind spots between products become unmonitored attack surfaces. Each vendor assumes the others are handling certain threats. Attackers exploit these assumptions.
And the cost explosion is real: three vendors, three contracts, three support organizations, three renewal cycles, three sets of professional services. Your security budget triples while your actual security posture deteriorates.
The Traefik Advantage: One Platform. One Binary. Three Gates.
Traefik delivers protocol-level MCP protection that addresses the security gap inherent in MCP's design with native TBAC enforcement across all MCP server types. True AI sovereignty means NVIDIA NIMs run entirely in your infrastructure. No external API calls. No vendor lock-in.
The platform works with your existing infrastructure, integrating seamlessly with your OAuth-compliant IdP (Okta, Azure AD, Auth0, Keycloak, etc), deployment patterns (Kubernetes, Docker, VMs), and monitoring tools. Production performance is guaranteed through sub-millisecond authorization using stateless JWT validation. No database queries, no external calls.
Unified observability lets you correlate attack chains across databases, file systems, CRMs, and communication platforms in a single platform. And this isn't theoretical. Traefik is battle-tested at scale, trusted by millions of deployments worldwide, proven in production environments.
Of course, no security solution is perfect. Traefik cannot fix vulnerable server code or prevent command injection vulnerabilities in poorly written MCP server implementations, though it provides comprehensive logging and behavioral monitoring to mitigate risks. It cannot secure vulnerable clients or fix security flaws in client-side implementations, but enforces policies regardless of client behavior. It cannot prevent sandbox escapes or stop runtime containment breakouts in underlying infrastructure, though TBAC limits the blast radius. And it cannot replace secure coding practices. Developers must still write secure MCP servers following security best practices.
What this means is that Traefik provides comprehensive protection for protocol-level and infrastructure-level threats across your entire MCP ecosystem. This covers the vast majority of real-world attack vectors. The remaining gaps require secure development practices and infrastructure hardening that no gateway can replace.
The Bottom Line
MCP adoption is accelerating faster than security teams can respond. Developers are deploying AI agents with access to Salesforce, Google Drive, Slack, databases, and dozens of other critical systems, often without security review.
The question isn't whether your organization will adopt MCP-based agents. The question is whether you'll secure them before or after a breach.
The cloud-native community learned security lessons through painful incidents. Apply those lessons to AI agents before your organization becomes the cautionary tale.
Next Steps
Traefik Labs has pioneered the Triple Gate Pattern, the industry's most unified and declarative runtime platform that delivers enterprise-grade AI security without operational fragmentation.
Ready to Secure Your Agentic Enterprise?
- Download the Complete Implementation Guide - Detailed technical documentation with code examples, configuration samples, deployment patterns, and testing procedures
- Schedule a Technical Briefing - See the Triple Gate Pattern in action with your MCP architecture and threat scenarios
- Request a Security Assessment - We'll analyze your MCP exposure and map TBAC policies to your agent workflows
Secure your agentic enterprise with Traefik's Triple Gate Pattern—available today, proven in production, ready to scale.