Simplified Security for Kubernetes with Traefik Proxy and Let’s Encrypt

Originally published: November 2019
Updated: April 2022
Network encryption – also known as transport layer security (TLS) – is a must for today’s online apps and services. Beyond the obvious need to prevent data breaches and other malicious attacks, there are also regulatory concerns to consider. Network encryption can be an important step in proving GDPR compliance, passing a financial audit, or complying with domain-specific regulations such as HIPAA or PCI DSS, to name just a few examples.
Unfortunately, getting encryption right is a non-trivial matter, and throwing containers and Kubernetes into the mix only compounds the issue. The distributed nature of Kubernetes environments and the often-brief lifecycles of containerized workloads both multiply the challenges of network security.
Still, there’s hope. Newer tools and services – including Traefik Proxy and Let’s Encrypt — can make the process of securing Kubernetes clusters simpler, speedier, and more resilient.
Lowering barriers to encryption
Historically, network encryption has been both laborious and costly. By some estimates, managing a typical certificate and private key can take four hours per year. That may not sound like much, but when multiplied by the requirements of a large infrastructure, this essential maintenance can quickly become burdensome, particularly given the current push by Apple and other vendors to limit the validity of certificates to no more than 398 days.
The alternative, however, is even worse. Expired or invalid certificates can lead to outages and reduced service, resulting in untold losses in productivity and revenue.
Let’s Encrypt was founded to address these issues. A project of the Internet Security Research Group, Let’s Encrypt is a free, nonprofit, automated, and open certificate authority (CA), created with the goal of promoting universal internet security and data privacy through encryption. Its sponsors include some of the largest software vendors and online services in the industry.
Let’s Encrypt will issue an unlimited number of domain-validated certificates with 90-day validity to the owner of any domain name, free of charge. As of this writing, the project has issued more than 1 billion certificates and it counts some 200 million websites as its clients.
Automation: Let’s Encrypt’s secret sauce
Cost reduction is of course welcome, but the most important benefit of Let’s Encrypt is labor reduction via automation. For Kubernetes operators, automation is a way of life. Let’s Encrypt brings that spirit to the world of network security. Central to how Let’s Encrypt works is the ACME (Automated Certificate Management Environment) protocol, which was made an IETF standard in 2019. It defines a method whereby a computing service and a CA (typically Let’s Encrypt itself) can complete the process of requesting, issuing, and verifying certificates without manual intervention.
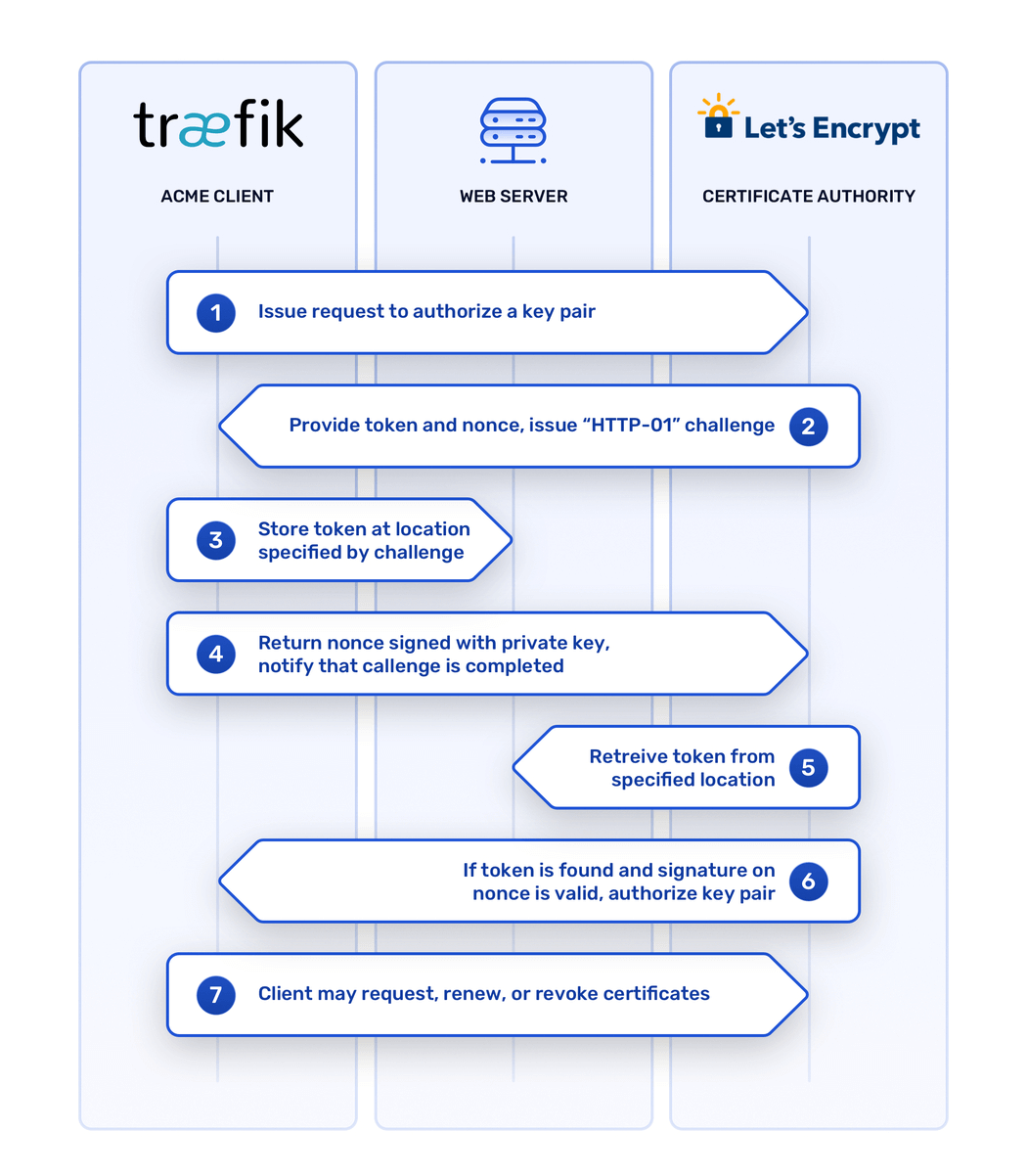
The ACME domain validation process relies on public key cryptography to establish trust. ACME client software, also known as a certificate management agent, generates a public-private key pair and presents it to a server on the CA’s end, along with a domain name. The server then asks the client to prove that it controls the domain in question by satisfying one or more challenges. If the client completes the challenges and signs some temporary data (a “nonce”) with its private key, the server gives the client’s key pair its stamp of approval.
Once the client has an authorized key pair, it can use it to request, renew, or revoke certificates from the CA, as long as the keys remain valid. Automating these tasks can eliminate as much as 95% of the labor involved in managing TLS encryption.
ACME and Traefik Proxy
So how to get this level of automated certificate management for a Kubernetes cluster? One of the easier ways is to deploy the open source Traefik Proxy edge router as a Kubernetes Ingress controller. Traefik Proxy includes a built-in ACME client, so no additional software is needed to begin working with Let’s Encrypt.
When used as an Ingress controller, Traefik Proxy ferries requests from the external network to services running within the Kubernetes cluster, using routes defined by Kubernetes Ingress resources. Traefik Proxy’s ACME client can automatically request and provision certificates for any domain assigned to the cluster, making it possible to add TLS-encrypted routes.
Traefik Proxy aims to reduce setup times by automatically discovering the right configuration for a given infrastructure, so putting the pieces in place is straightforward. Instructions on how to install Traefik Proxy into a Kubernetes cluster and enable Let’s Encrypt are available in the official documentation.
A secure starting point
Traefik Proxy and Let’s Encrypt together offer to set up basic TLS routing for Kubernetes. As mentioned earlier, however, encryption for network security is a non-trivial matter, particularly in more complex environments. Just for starters, you’ll need genuine domain names that point to servers that are accessible by the public internet for Let’s Encrypt’s domain-validation challenge process to work.
Further challenges arise when you want to run more than one instance of Traefik Proxy, to ensure high availability. It’s currently not possible to run more than one instance of the community-maintained version of Traefik Proxy on a cluster with Let’s Encrypt enabled because there’s no guarantee that any request will be handled by the correct instance of Traefik Proxy. One way to address this is to use the commercial Traefik Enterprise Edition (TraefikEE) product, which offers distributed Let’s Encrypt as a supported feature.
Here's a short video of how mTLS works and how it is deployed using Traefik Enterprise:
Organizations with more specific needs – such as interfacing with enterprise vault providers – and who aren’t afraid to take a hands-on, DIY approach may need to install additional, dedicated certificate management software. One such option that’s proven popular is cert-manager, which can work in tandem with both Traefik Proxy and Traefik Enterprise.
The key point, however, is that TLS encryption should be everywhere, and today it can be. The ACME protocol, Let’s Encrypt, and self-configuring software like Traefik can automate away much of the hard work that was once involved with certificate management and secure request routing. In turn, that frees you to concentrate on what really matters, which is how to deliver the most value with your services, rather than how to secure them.
You can try out the features of Traefik Enterprise, including distributed Let’s Encrypt, by starting a 30-day free trial.



