Announcing Traefik Proxy 2.6
With HTTP/3 enhancements, inflight request middleware for TCP routers, updates for the Kubernetes Gateway API, and more.

We are very happy to announce the general availability of Traefik Proxy 2.6, the latest update to our cloud native edge router and application proxy solution.
This release is focused on maintaining support for cutting-edge technologies that allow our users to prepare for the future.
Let’s take a closer look at the features shipped with Traefik Proxy 2.6!
Kubernetes Gateway API update
We are updating our Kubernetes API Gateway provider following the release of the upstream 0.4.0 API by the Kubernetes team.
This not only updates the API version from v1alpha1 to v1alpha2 but also brings some highly-anticipated additions. To name a few, Traefik Proxy 2.6 changes the way gateways bind to routes and allows for safer cross-namespace references following CVE-2021-25740.
Although the Kubernetes Gateway API is alpha in Kubernetes, it will one day replace the Ingress subsystem with a role-oriented structure that delegates responsibility and control to the actual people doing the work. Users of Traefik Proxy have the opportunity to test this new functionality while developing a strategy for empowering their teams and switching to the Gateway API when it’s ready.
We are preparing a detailed article about the new features and how you can start using them, which will be released in February.
HTTP/3 enhancement
With Traefik Proxy 2.6, it is now possible to configure the advertised UDP port of an HTTP/3-enabled entrypoint. This allows Traefik Proxy to specify the port where an external load balancer is listening, when that port is different from the one where Traefik Proxy is listening. This is particularly important in Kubernetes, where working around limitations in the LoadBalancer Service requires this option.
Here’s an example:
experimental:
http3: true
entryPoints:
name:
http3:
advertisedPort: 443
This feature will also be covered in detail in two future blog posts, so stay tuned.
Consul Enterprise support
Traefik Proxy 2.6 adds the first round of support for Consul Enterprise and the HashiCorp Cloud Platform (HCP). This includes an experimental implementation of the namespace feature for the Consul K/V and Consul Catalog providers. This feature allows you to specify a target namespace other than the default namespace when connecting to Consul.
You can use this feature immediately to isolate shared Traefik Proxy configuration items, such as middleware declarations and static routing for the dashboard, external apps, or metrics.
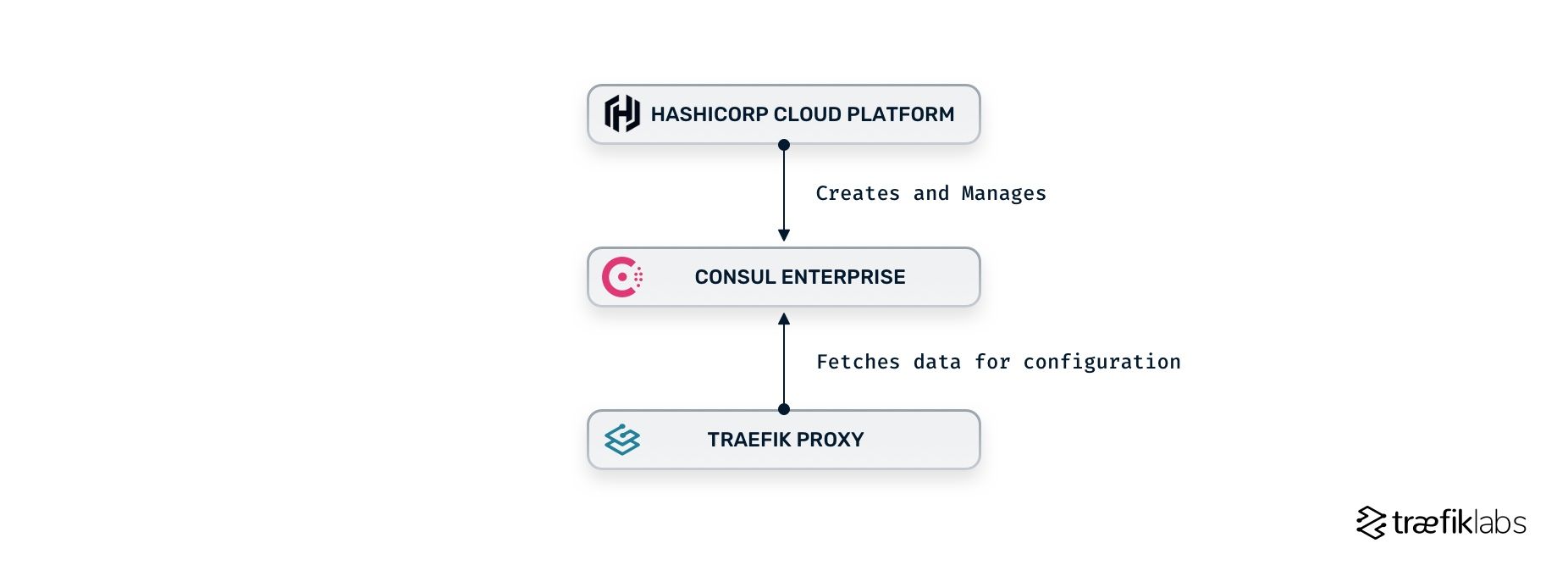
You can also provide the HCP admin token to Traefik Proxy, which is required when connecting with Consul Enterprise instances deployed on HCP.
Example:
providers:
consulCatalog:
namespace: "apps"
endpoint:
address: 127.0.0.1:8500
consul:
namespace: "traefik"
endpoints:
- "127.0.0.1:8500"
Support for Consul Enterprise namespaces will arrive in two parts, and this is the first. Traefik Proxy 2.6 only supports one namespace definition per provider, and enhanced namespace support is planned to arrive in Traefik Proxy 2.7.
Your feedback is important! If you use HCP and/or Consul Enterprise, please test this feature in your environment and let us know if you encounter any challenges by opening an issue on GitHub.
We will have a more detailed blog post on Consul Enterprise Namespace support, including some hands-on examples, in the coming weeks.
Inflight request middleware for TCP routers
Following in the footsteps of its HTTP counterpart, this new middleware allows users to define an upper limit for the number of simultaneous connections to TCP routers inside of Traefik Proxy.
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-inflightconn
spec:
inFlightConn:
amount: 10
Grouping is based on the source IP address, and once the limit is reached, any further connections from that source will be rejected.
This is the second TCP middleware added to the core product but we’re already excited about exploring the possibility of adding more that could tackle more complex use cases, such as rate limiting and traffic shaping.
Do you use TCP routers in your environment? What middleware would you like to see added? Please let us know in the Forum or by opening an issue on GitHub.
Show me everything
There’s more in this release than we’re able to highlight here, and that’s why we have three detailed articles planned for the next few weeks. In these articles, we will go over the HTTP changes in 2.6, our updates for the Kubernetes Gateway API, as well as a walkthrough of our experimental feature for Consul Enterprise Namespace support. In the meantime, please check the complete CHANGELOG for all the details.
We also invite you to join the upcoming webinar, where we’ll discuss all the changes in Traefik Proxy 2.6 and answer any questions you might have. We’re looking forward to seeing you all there.
Next steps
We believe in the future of the Kubernetes Gateway API and HTTP/3. Our goal is for you to experiment and feel comfortable with the technology of tomorrow before it knocks on everyone’s door, and that’s why we’re building in support for that technology today.
We are also very excited about our partnership with Hashicorp, and we look forward to continued collaboration that improves integrations on both sides. When companies like ours work together, the users are the ones who win.
As always, we’d like to thank our amazing community and contributors — your work and passion are what make Traefik Proxy special!
For more information about Traefik Proxy, visit our documentation pages, or head out to our Forum for all the latest community topics.
Ready to try out Traefik Proxy 2.6? Learn how you can easily get started today.



