Announcing Traefik Enterprise 2.7
With OAuth 2.0 client credentials, PKCE support for OIDC, and API Portal enhancements.

The past month has been extremely busy here at Traefik Labs with one announcement coming after the other! In case you missed it, last month we announced our partnership with HashiCorp, launched the beta version of our new product, Traefik Hub, and just last week, we released the latest version of Traefik Proxy (2.8).
And we are proud to say that we have no intention of slowing down! Today, we come to you with yet another announcement — We are excited to present the latest version of Traefik Enterprise.
Traefik Enterprise 2.7 shipped with important new features and enhancements for authentication, Windows support, and API Portal. Let’s dig in and explore all the new features one by one.
OAuth 2.0 client credentials
There are certain use cases where machine-to-machine (M2M) tokens are used internally with the intention of opening APIs to external partners (B2B) while continuing to use one identity provider as the single OAuth2 authorization service.
With the 2.7 version, Traefik Enterprise now accepts credentials from the external client and then calls the identity provider (client_credentials flow) to obtain the access token. The credentials accepted are in the form of a clientId and a clientSecret. Traefik Enterprise caches those tokens and attaches them when forwarding the request upstream while all subsequent requests from the same external client re-use the same cached access token until it expires.
Having privacy and cost issues in mind when implementing this solution, we made sure that:
- External partners will not be aware of and concerned with which identity provider an organization is using.
- External partners will not be able to excessively request new M2M tokens resulting in additional costs, as some identity providers charge for the number of M2M tokens issued.
Let’s take a look at the steps you need to follow to use this feature.
- Declare your authentication server address and your KV Store in the Static Configuration:
# Authentication Source
authSources:
clientCredsSource:
oAuthClientCredentials:
url: https://auth.server.com
# Consul K/V Store
stores:
consulStore:
# the value has to match one of the possible
# kv store types (consul, etcd, zookeeper, and redis).
consul:
keyPrefix: traefikee
endpoints:
- 'localhost:8500'
- Configure your middleware in the Dynamic Configuration:
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-client-creds
spec:
plugin:
oAuthClientCredentials:
# Authentication Source to use
source: clientCredsSource
# KV Store
store: consulStore
audience: https://api.example.com
PKCE support for OIDC
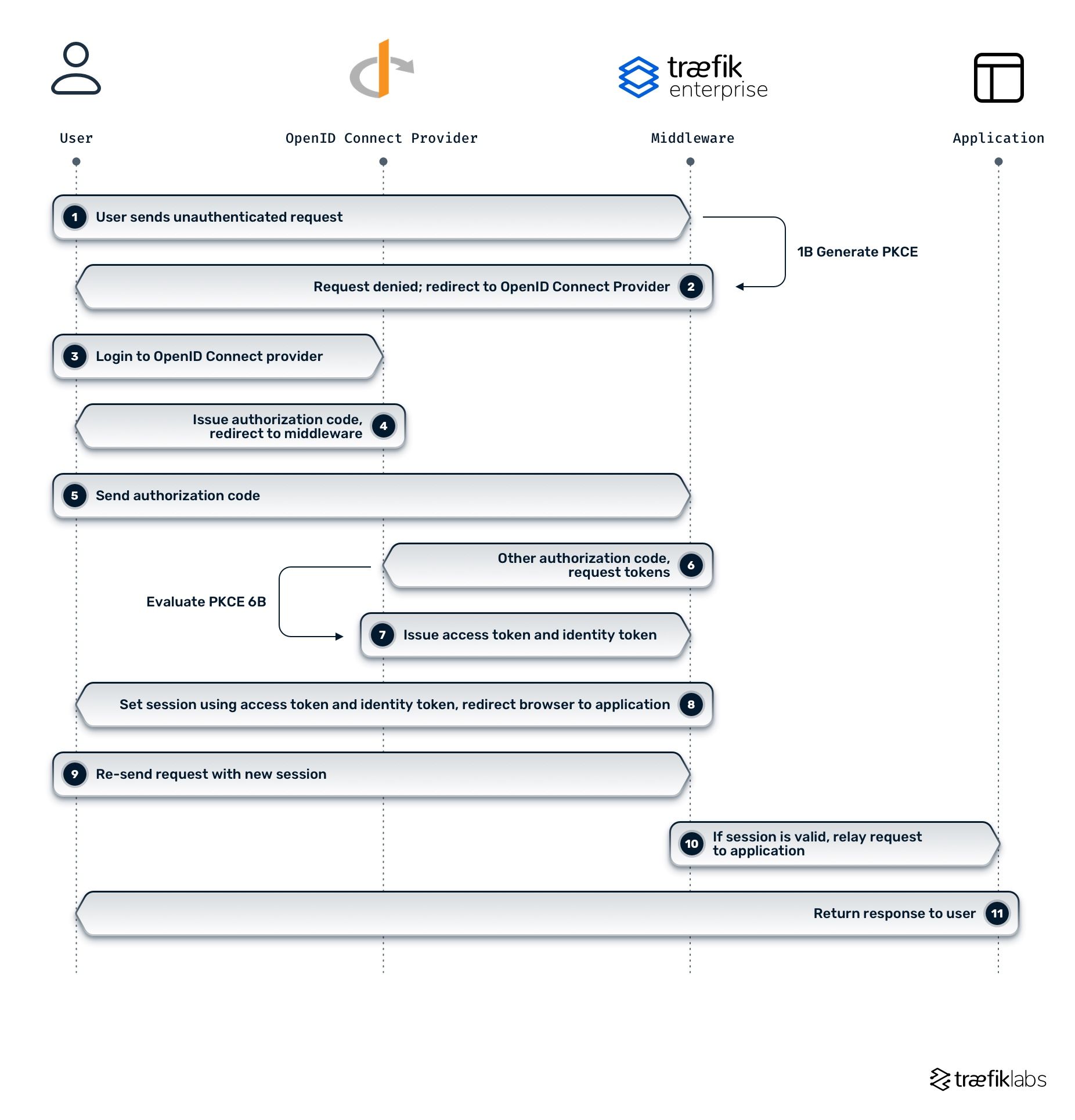
Proof-Key for Code Exchange (PKCE) prevents authorization code injection and adds an extra layer of security to the authorization code flow and helps mitigate a number of security threats, making it very useful for all OAuth clients. With the release of Traefik Enterprise 2.7, the OIDC middleware now supports PKCE.
The regular authorization code flow and the auth code flow with PKCE are very similar, but in the latter, PKCE is added to a couple of steps within the flow. The process is automatically generated by Traefik Enterprise and evaluated by the Identity Provider — the user is not required to take any action:
- The user sends the request to Traefik Enterprise.
- Traefik Enterprise generates the PKCE code verifier and challenge and then redirects the user to the Identity Provider sign-in page. This redirect includes the code challenge.
- The user authenticates.
- The authorization server redirects back to Traefik Enterprise with an authorization code.
- Traefik Enterprise sends the authorization code to the Identity Provider, including the code verifier that was generated in the second step.
- The Identity Provider evaluates the PKCE code and returns access and ID tokens.
- Traefik Enterprise uses these tokens to call the resource server on behalf of the user.
- The user sends the request with the new session to Traefik Enterprise which validates the request and sends it to the application.
The diagram below summarizes these steps.
Running Traefik Enterprise on bare-metal Windows host
Up until now, it hasn’t been possible to deploy Enterprise on Windows machines. Neither the CLI nor the nodes have worked on Windows machines. By popular demand, we now made it possible to deploy a Traefik Enterprise cluster on Windows machines.
This feature brings global Windows support for both the cluster and the CLI.
To manage your cluster on Windows, install teectl and start your journey just like you would on a Linux machine.
Test APIs from the API Portal
With Traefik Enterprise 2.7, you are now able to test your API shown in the API Portal directly from the browser, eliminating the need for a client.
To use this feature, follow these steps illustrated in the short walkthrough video:
- Enable the API Portal on your cluster, using the dedicated option in the Traefik Enterprise configuration
- Open your API Portal
- Select the API to test in the menu
- Select a method (POST or GET, for example)
- Click on the button Try Out
And, voilà!
Next steps
This Traefik Enterprise release brings a lot of important features that tackle some real-life production challenges. And, as always, we are not stopping there — we have a lot more planned for future releases!
Currently, we are actively working on more API Portal updates, improving our integration with HashiCorp Vault namespaces (first introduced in Traefik Enterprise 2.6), and last but not least, we are working on even more improvements and enhancements for the OIDC middleware, more specifically, adding support for distributed claims. So, stay tuned!
In the meantime, if you’re new to Traefik Enterprise and want to learn more, don’t hesitate to reach out to request a demo or put your skills into action with a free, 30-day trial. And for more information, feel free to dig into our documentation.



